This article posted byMiniTool partyelaborates onmalware detection and removalwith its definition, necessity, and techniques.
It also discussesmalware prevention and detectionwith malware removal tools and a backup program to keep data safe.
What Is Malware?

Sometimes, it pretends to be a legitimate program before finally attacking your machine.
Malware can get into your gear in multiple methods.
Once arrived at your machine, in most cases, the malware will hide itself firstly.

Then, it will penetrate your gear files, folders, apps, or locations one by one.
Finally, it will get into the core of your machine the OS and carry out attacks.
Malware is one of the biggest threats on the Internet.
![[Review] Fileless Malware: Definition/Detection/Affect/Removal](https://images.minitool.com/minitool.com/images/uploads/2021/04/fileless-malware-thumbnail.jpg)
What Is Malware Detection?
Generally, malware detection is the process of scanning a target machine or files to find malware.
It is created specifically against malware.

Relying on many techniques and tools, malware detection is reliable and effective.
Instead of a simple one-way process, malware detection is more complex than it seems to be.
Yet, it wont take long to complete a detection process of malware.

Why Need Malware Detection?
Once malware is detected, a warning message will be sent and received by users.
Therefore, the users will stop diving deeper into the insecure website or downloading unknown files.
![[Wiki] Microsoft System Center Endpoint Protection Review](https://images.minitool.com/minitool.com/images/uploads/2021/05/system-center-endpoint-protection-thumbnail.png)
Thus, it will effectively keep hackers from controlling your gadget and stealing your information.
Types of Malware Detection
There are many kinds of malware detection methods.
Lets learn them all and have a thorough understanding of the history ofmalware detection techniques.
The signature database is used to compare subsequent malware incidents.
When a file is found suspicious, the antivirus will look for patterns that match a known malware.
If a match is found, the file will be blocked, isolated, or removed.

Signatures were the mainstay of malware detection technologies for many years.
And, they are still useful for detecting known threats.
However, when new unknown malware attacks, signatures can help little.

Today, signature-based detection is no longer an effective way due to constantly evolving malware.
modern malware takes advantage of multiple new techniques to escape from detection.
This makes it harder to find the malware by matching its signature with known malware.

How does fileless malware work?
How to detect fileless malware?
How to remove fileless malware?
![[Complete] List of Samsung Bloatware Safe to Remove](https://images.minitool.com/minitool.com/images/uploads/2021/05/list-of-samsung-bloatware-safe-to-remove-thumbnail.png)
Technologies have taken by modern malware:
1.
Polymorphism
Polymorphic malwarechanges its features all the time to prevent being detected.
Its creators make use of polymorphism to evade pattern-matching checking of antivirus tools.

Nowadays, most malware programs adopt polymorphism to change their signatures each time they iterate.
So, these variants are undetectable by signature-based malware detection even they are based on known malware families.
Code Obfuscation
Obfuscation of code is another way used by modern malware to avoid detection.
Therefore, using legitimate tools in suspicious processes is an indication of malware infection.
Since signature-based analysis is less effective than before, newadvanced malware detectiontechniques must be created and they are.
#2 Sandbox
Sandbox technology detects malware by testing potentially malicious code in an isolated virtual environment.
Yet, sandboxing has some shortcomings.
Besides, some malware variants are designed to exploit the vulnerabilities of sandboxes.
Whats more, thisbehavior-based malware detectionsets some challenges to its program like costing much time.
Heuristic analysis establishes a baseline of normal activity for the system or software.
Then, if something different happens, it will be regarded as a potential threat by heuristic analysis.
Is Win32:Bogent a virus?
you might find the answer from this post.
It will also show you how to deal with Steam false positive and real virus infection.
Heuristic analysis is one of the few technologies that are able to detect polymorphic malware.
So, hackers cant update their malware accordingly.
Also, heuristic analysis has drawbacks.
One of its disadvantages is that it is useless for malware whose code is sufficiently obfuscated.
Newer and more advanced technologies are needed.
Therefore, several next-generation antivirus (NGAV) techniques have come into being.
What are System Center Endpoint Protection definitions?
What are the features, usages, workflow of Endpoint Protection?
Read this article to learn more.
It is very useful to deal with threats likezero days.
However, the whitelist frustrates end users by preventing them to run completely safe applications.
Thus, whitelist tech is only recommended in high-risk environments.
Those behaviors include how long a file needs to open, file traffic, file daily behavior…
Though being intelligent and highly automatic, machine learning isnt perfect to detect malware.
Therefore, it cant be used solely for malware detection.
Instead, it is recommended that utilize machine learning together with other mature or traditional detection technologies.
How to Tell Whether My Computer Is Infected by Malware or Not?
The above malware detection methodologies are somehow sophisticated for general users.
Then, the following are some common symptoms if you are infected with malware.
Below just lists the common malware types.
It requires a host program and can cause great damage.
Some examples are Creeper,Conficker, Mirai, Win32/Simile, Gammima, and CiaDoor.
Whats the difference between malware and virus?
This post focuses on malware vs virus and you could read it to learn much information.
Some examples are CryptoLocker,Mercury,WannaCry,Ryuk,PXJ,Sodin, and Petya.
An example of spyware is CoolWebSearch (CWS).
It is usually bundled with a wanted program.
all can be a PUP.
What will be the biggest malware threats to businesses in 2019?
This post will show you the top security trends for 2019.
Worm
It is a standalone malware computer program that replicates itself to spread to other computers.
Unlike a virus, it doesnt need a host program.
Some examples areILOVEYOU, Stuxnet, SQL Slammer, andMydoom.
Trojan
A trojan horse can be any malware that misleads users of its true intent.
Usually, it spreads by some form of social engineering.
The detected trojans include but are not limited to DarkComet,Zeus, Zlob, Dyre, andMEMZ.
For example, Stoned Bootkit and Alureon (aka TDSS) are both rootkits.
Trojan can be used to create vulnerabilities in a equipment and install a backdoor.
Some examples are Sobig, Mydoom, Sony/BMG rootkit, and OpenSSL RSA.
It is reported that Microsoft has discovered a fileless malware campaign that spreads Astaroth backdoor to infect victims.
Keylogger is often used to steal passwords or other confidential info.
Some keyloggers are Blue Kill, Zeus, SpyEye, Inputlog, Scriptlog, Translog, and FlashCrest iSpy.
Some well-known computer exploits are Rig, GreenFlash Sundown, Fallout, Magnitude, GrandSoft, andZero-day.
So, it can also be called cryptomining.
Cryptojacking can result in computer slowdowns and crashes due to straining of computer resources.
Malvertising
14.
Crimeware
Crimeware is a class of malware developed especially to automate cybercrime.
An example of crimeware is Bankash.G trojan.
Some bots are good while others are used to launch malicious attacks.
A spambot is a software program designed to assist in the sending of spam.
Spybot worm is a large family of computer worms of varying characteristics.
Unwanted bundled software, also calledbloatwareor crapware, can include major security vulnerabilities.
What are the lists of Samsung bloatware safe to remove?
How to create your own Samsung bloatware list?
Stalkerware
Stalkerware is monitoring software or spyware used for stalking.
It is mostly used in smartphones.
Some examples are Monitor.AndroidOS.MobileTracker.a, Monitor.AndroidOS.Cerberus.a, Monitor.AndroidOS.Nidb.a, Monitor.AndroidOS.PhoneSpy.b, and Monitor.AndroidOS.XoloSale.a.
All above malware detection techniques need to be embedded into a malware detection tool to be available.
And, such a tool is the same one that allows you to remove the detected malware.
That is to say, you use a single tool to detect and remove malware.
Many of the above programs aremalware detection freeor have free versions.
There is nobest malware detection software, only the most proper one.
Just choose the one that suits you and satisfies you.
Besides those offline malware detection programs, there is alsoonline malware detectionlikemalware detection websites.
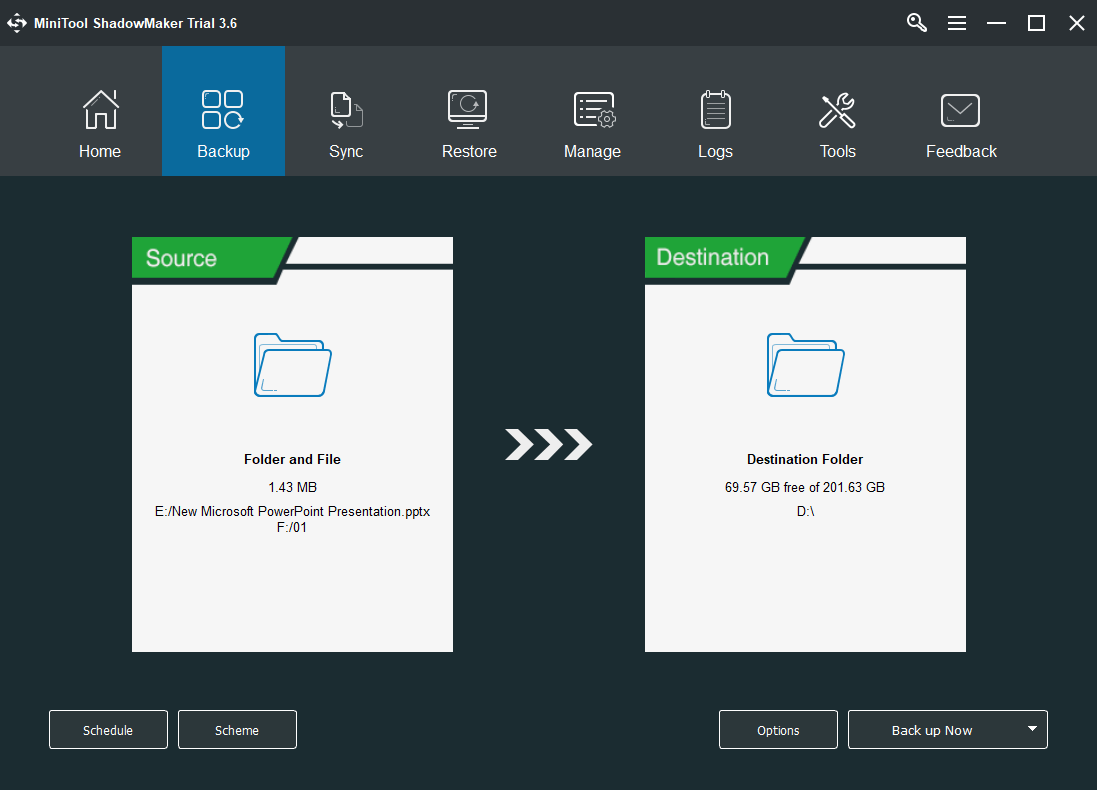
How to Protect your rig from Malware?
Another copy or more copies give double insurance to crucial files.
Generally, such methods contain multiple protection layers and levels to detect and beat viruses.