What Is Conficker?
It becomes the largest known computer worm infection since Welchia in 2003.
Conficker was first detected in November 2008.
![[Review] MyDoom Virus: The Most Destructive & Fastest Email Worm](https://images.minitool.com/minitool.com/images/uploads/2021/03/mydoom-virus-thumbnail.jpg)
Although Conficker propagated widely, it didnt cause much damage.
The reason is that maybe its designer didnt dare to use it for the virus drew much attention worldwide.
Conficker doesnt destroy or steal data.
![[Review] What Is the ILOVEYOU Virus & Tips to Avoid Virus](https://images.minitool.com/minitool.com/images/uploads/2021/02/iloveyou-virus-thumbnail.jpg)
How Does Conficker Come From?
However, Joshua Phillips, a Microsoft analyst, offers another interpretation of the name conficker.
What is the MyDoom Virus?

How does MyDoom develop?
How to prevent MyDoom from further spreading?
Conficker had spread across administrative offices, NavyStar/N* desktops on various Royal Navy submarines & warships.

And, it was reported that over 800 machines were infected across the city of Sheffield.
Intramar, a French Navy computer online grid, was infected with Conficker on January 15, 2009.
The memo was from the director of the service and was leaked subsequently.

It called for users to avoid connecting any unauthorized equipment to the web link.
In January 2010, the Greater Manchester Police computer connection was infected.
What did it do?

When did it start and how did it stop?
Who created it and in what language was it created?
Find all answers here!
What Does the Conficker Virus Do?
Also, the developers of Conficker were tracking anti-virus actions from data pipe operators.
Thus, they released new versions to patch the malwares own flaws.
Conficker B and later may also attach to a running Windows Explorer process.
Yet, attaching to those processes might be discovered by the trust feature of an installed firewall.
Windows utility used by malware?
To know more information about this situation, you’ve got the option to read this post.
They can remotely execute copies of themselves via the administrative share on computers visible over NetBIOS.
Conficker Propagation
Conficker has a few mechanisms to pull or push executable payloads over the connection.
Those payloads are used by Conficker to update itself to newer versions and install additional viruses.
Version A generates a list of 250 domain names each day across 5 TLDs (Top-Level Domain).
Malware is one of the biggest threats on the Internet.
This post provides information about different types of malware and you might know how to avoid them.
The new pull mechanism is unlikely to spread payloads to more than 1% of infected computers each day.
Yet, it is expected to function as a seeding mechanism for Confickers peer-to-peer (P2P) data pipe.
Conficker Self-Defense
Besides the wonderful infection and propagation mechanisms, Conficker also has advanced self-protecting systems.
Its Version B, C, D, and E can block certainDNSlookups and disable AutoUpdate.
Especially, Variant D does an in-memory patch of DNSAPI.DLL to block lookups of anti-malware-related sites.
Is Vimms Lair safe to use and download old video game ROMs, emulators, or manuals?
What websites are Vimm.net alternatives?
How to keep safe while using Vimm?
Version D of Conficker also disablesSafe Mode.
Moreover, each version of Conficker ends up updating itself to the next version or higher versions.
Though Conficker wont cause data loss to victims, it does increase the data pipe payload of them greatly.
Thus, the infected computers will experience slow web connection performance and it will influence the usage of them.
How to Avoid Conficker?
How to Avoid Being Infected with Conficker?
Then, how to protect yourself from being infected by Conficker?
Below suggestions are listed for your reference.
Therefore, you have shut down the backdoor for the malware.
How to determine whether your system is vulnerable to Conficker or not?
Generally, if you are using Windows 7 or later edition, you are safe from Conficker.
Just revamp your OS will solve the problem!
Whats Avast Virus Chest?
How to check/view Avast Virus Chest?
How to restore files from Avast Virus Chest?
How to delete a file from Avast Virus Chest?
What should you do?
Never use a USB or open a shared file?
you might still use USB and shares since they are unavoidable nowadays.
Thus, you dont have a chance to scan it for viruses.
In such a situation, you shouldturn off the autorun serviceof your system for external media like USB.
is a lifetime task.
No one can do it manually or alone.
As far as this article was written, no version of Conficker causes data loss to its infected computers.
Yet, no one can guarantee that there is also no data loss due to Conficker.
It may update itself and start to destroy victims files in the future as most modern computer malware do.
If so, what can we do for the preparation of the possible damage?
Our purpose is to avoid losing data.
Then, how to quickly make copies of files in a reasonable manner?
Lets see how it works.
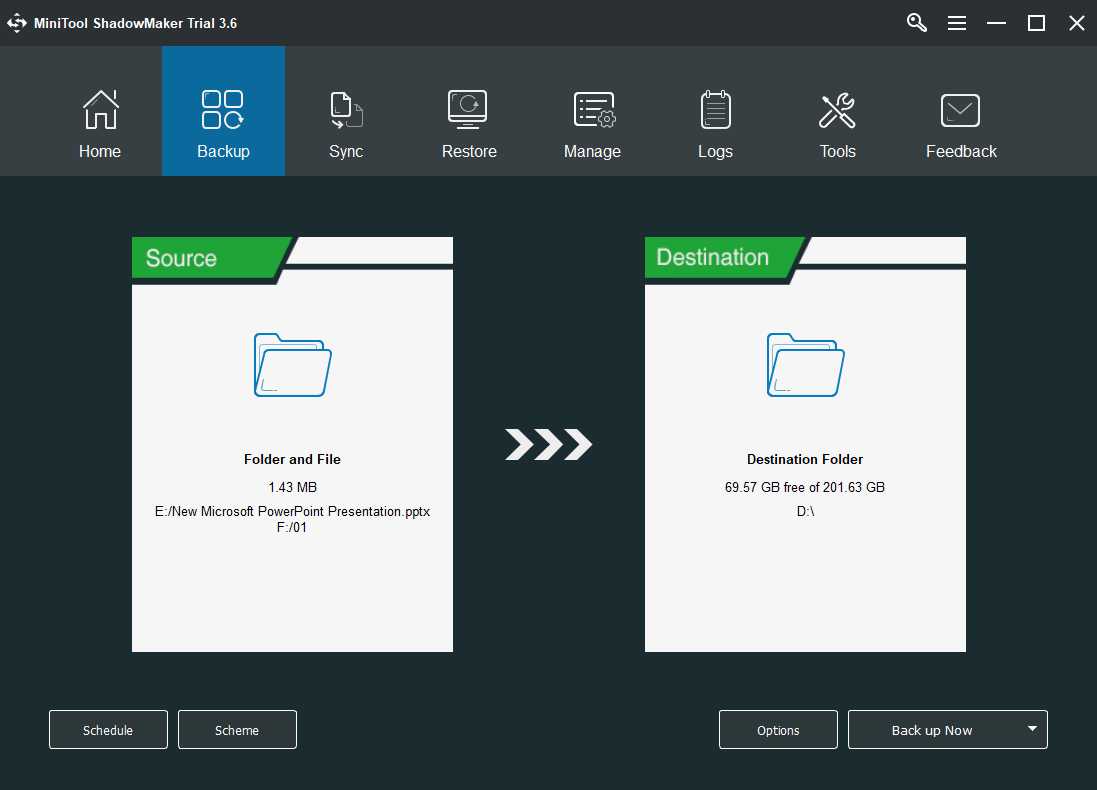
Download and install MiniTool ShadowMaker on your machine.
MiniTool ShadowMaker TrialClick to Download100%Clean & Safe
Step 2.
Launch the program and clickKeep Trialto try its wonderful features.
In its main interface, clickBackupin the upper menu.
In the Backup screen, click theSourcemodule to snag the items you plan to back up on your machine.
Then, click theDestinationmodule to specify where to save the backup image.
External storage place is recommended.
Also, note that the target storage location will be overwritten.
Check the backup task.
If youd like to back up those source files regularly, just set ascheduled backupfor them by clicking theSchedulebutton.
Finally, confirm the task by clicking theBack up Nowbutton in the lower right.
The backup task will start after another confirmation.
Then, just wait for the success of the procedure.
Once finished, just exit the app.
Ok, the above is all about the Conficker worm Id like to share in this article.
If you want to read more related information, just search on this website.
If you have anything about Conficker to discuss, just use the below comment section.