What Is a Firewall?
First of all, you should have a basic knowledge of thefirewall.
Maybe, you are interested in this post Top 10 Anti Hacking Software to Protect your box.
Nowadays, there are many types of firewalls and maybe you dont know which one to choose.
Thus, in the next part, I will introduce the detailed information about the several types of firewalls.
it’s possible for you to know the advantages and disadvantages of each one.
Then, you might know which one you should choose.
Different Types of Firewalls
Types of Firewalls
What are the different types of firewalls?
What are the 3 types of firewalls?
These questions are often asked.
Packet-Filtering connection Firewalls
Packet-filtering connection firewalls are also called traditional connection firewalls.
They help to prevent unwanted traffic from entering the corporate connection to provide necessary connection protection.
The firewall simply checks packets passing through the router.
Advantages
Disadvantages
2.
It cant easily support all applications, and it will reduce the performance of protected applications for end-users.
Typical UTM functions include traditional firewalls,intrusion detection systems, Internet gateway security, and URL blacklists.
It may not provide the same level of protection as a more complex product.
4. online grid Segmentation Firewalls
online grid segmentation firewall is also one of the firewall types.
It may cause performance and availability issues and may cause the failure of some web link services.
It can protect the online grid, applications, databases, and other IT resources.
Database Firewalls
Database firewalls are a subset of web system firewalls.
They are usually installed directly in front of the database server they protect.
They are designed to detect and prevent specific database attacks.
These attacks may lead attackers to access confidential information stored in the database.
It monitors and audits database access and generates compliance reports for regulatory purposes.
Circuit-Level Gateways
Circuit-level gateways use another relatively fast method to identify malicious content.
It can save sources.
It doesnt check the packet itself.
Stateful Multilayer Inspection Firewall
Stateful multilayer inspection firewalls combine packet inspection technology with TCP handshake verification.
Compared with other firewalls, it can provide a higher protection level.
Stateful inspections and firewalls that use this technology usually reject any traffic between trusted and untrusted interfaces.
Thus, before choosing the firewall, you should conduct a security policy review and evaluation.
MiniTool ShadowMaker also supports restore Windows backup to a different PC with dissimilar hardware.
This post How Can You Do Windows Backup Restore to Different Computercan help you do that.
Now you’re able to download and try MiniTool ShadowMaker Trial Edition to do the backup task.
you’re free to use another feature of MiniTool ShadowMaker to back up files: Sync.
Here is how to sync files:
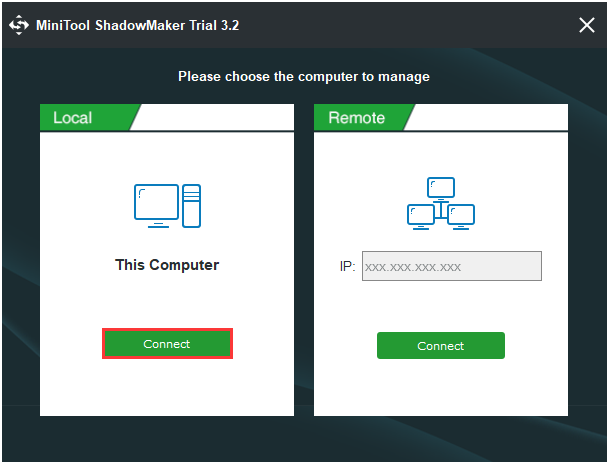
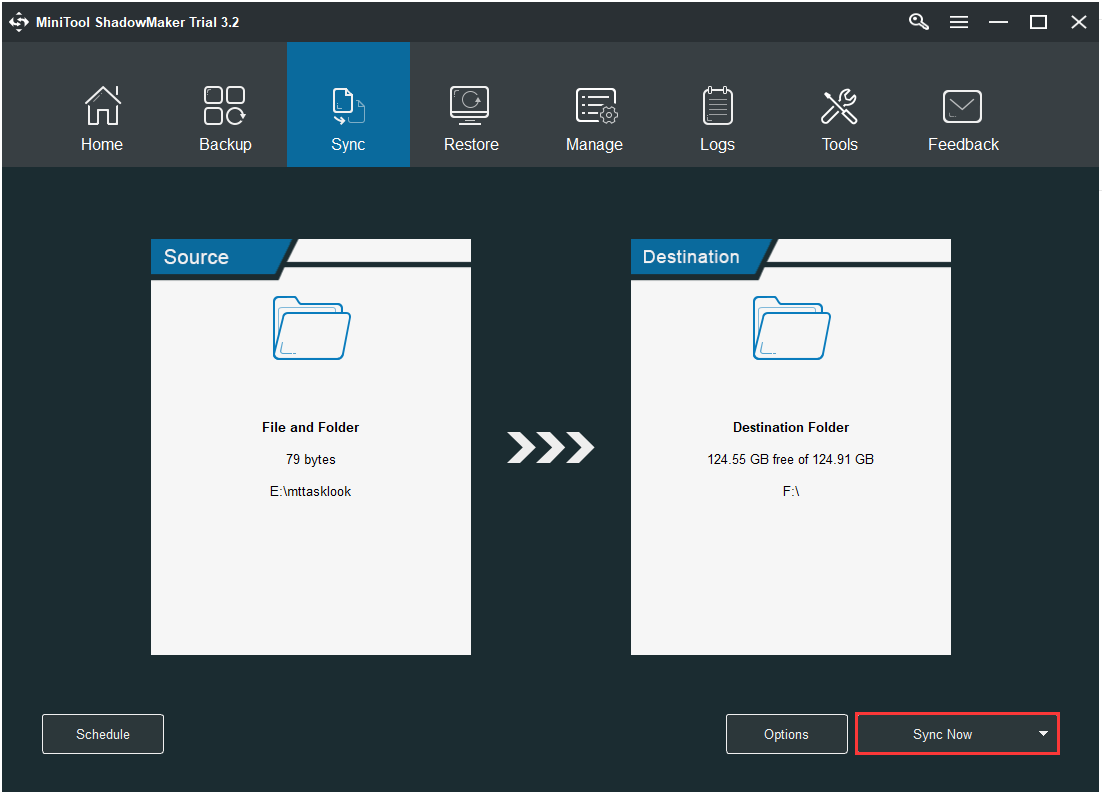
Step 1:After launching MiniTool ShadowMaker, go to theSyncpage.
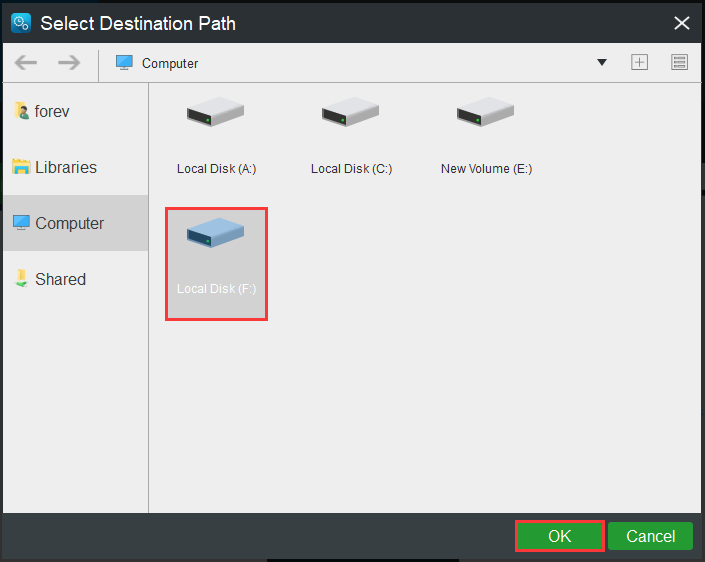
Step 2:Click theSourceandDestinationmodule to choose the files that you want to sync and the storage path.
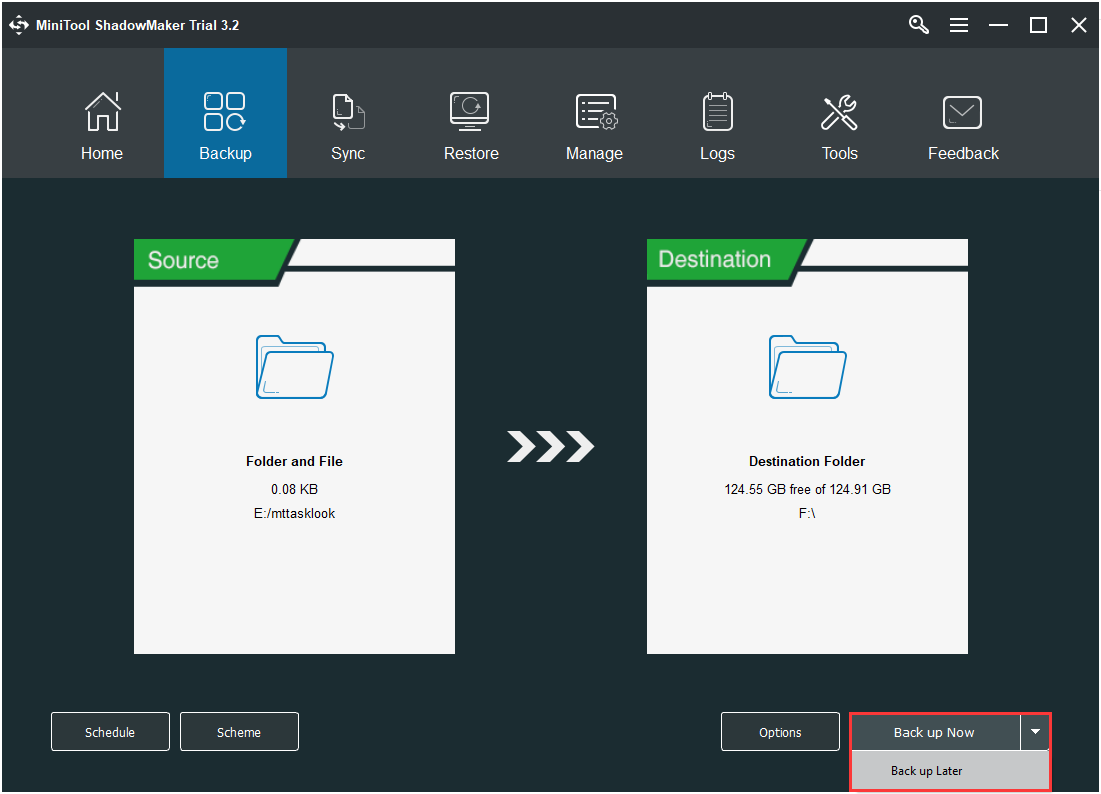
Step 3:Click theSync Nowbutton to immediately perform the sync process.
If you have any problems when you are using our program, c’mon let us know.
Or if you have any suggestions, also tell us.
Sending an email to[email protected]or leaving a comment below is available.
Types of Firewalls FAQ
Here are some tips for you to kill a firewall.