Therefore, you might easily tell that not all hackers are regarded as malicious enemies.
What Is White Hat?
Many enterprises and governments are dying for those professionals to ramp up their defense walls.

Those White Hat hackers often get highly paid and they can also work for personal interest.
What Is Black Hat?
Malware is one of the biggest threats on the Internet.
This post provides information about different types of malware and you might know how to avoid them.
White Hat Hacking
1.
Reconnaissance and research
This involves doing research on the organization to find vulnerabilities in the physical and IT infrastructure.
Black Hat Hacking
Black hat hackers techniques are constantly evolving but the main attack methods wont change too much.
Here is a list of hacking techniques you may encounter.
To learn more details about DDoS attacks, yo refer to this article:What Is DDoS Attack?
How to Prevent DDoS Attack.
Trojan virus
What is a Trojan virus?
What does a Trojan virus do?
How to remove the Trojan virus from your gear?
This post shows you the answers.
It is one of the most effective methods for identifying vulnerabilities.
Stage 4: Maintaining access
It is the process where the hacker has already gained access to a system.
The vulnerability analysis helps in analyzing, recognizing, and ranking the vulnerabilities.
Black Hat hackers
How to Protect Yourself from Black Hat Hackers?
you’re free to just turn them on only when you need them.
Choose Your Apps Wisely
Apps are a common channel to hide malicious codes.
Besides, just remember to tune up your apps regularly and timely remove those unneeded programs.
Use a Password, Lock Code, or Encryption.
MiniTool ShadowMaker has devoted itself to this field for years and sees greater advances and breakthroughs.
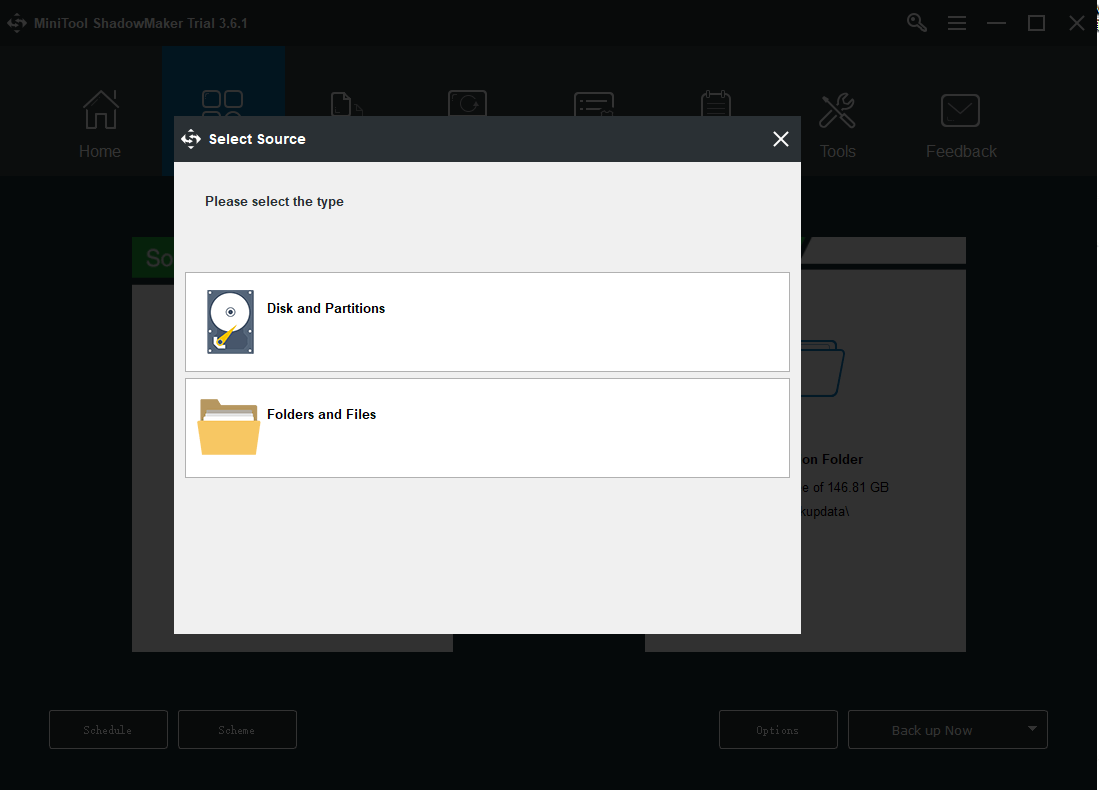
By default, the system has been set as the backup source already.
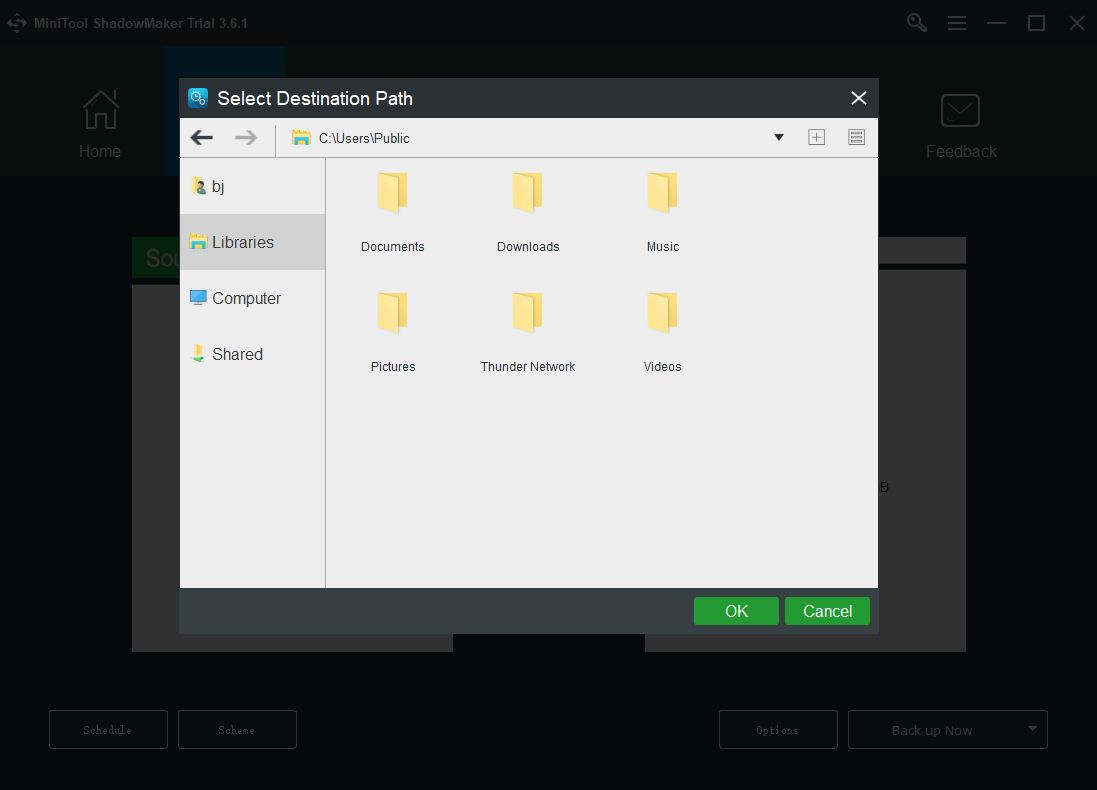
Then choose your destination path.
And then clickOKto store your changes.
The delayed backup task is on theManagepage.
Besides, with MiniTool ShadowMaker, you might sync your files or clone disk.
The services you’re free to enjoy are more than backup.
This article has described details about White Hat vs Black Hat and how to block hackers.
Anyway, some methods can help you minimize the loss and a backup plan can be your last resort.
If you need any help when using MiniTool software, you may contact us via[email protected].
White Hat vs Black Hat FAQ
White hats deserve legal respect.
The CEH is a vendor-neutral credential, and CEH-certified professionals are in high demand.
There are several ways to earn money as a black hat.
Some of them are hackers for hire; basically online mercenaries.