You may not hear about social engineering attack in your daily life, but it is very common.
This article onMiniTool Websitewill answer this question.
You cant be too careful about that.

What Is Social Engineering Attack?
It is universally acknowledged that personal information is more and more important in daily life.
The attackers make use of social communication skills to ask you some questions without your knowledge.

Types of Social Engineering Attacks
There are 5 types of social engineering attacks in total.
Well introduce them one by one in the following pages.
Scareware
Scareware is also called ransomware or deception software.
All their attempts are to invade your PC and steal your personal data.
Pretexting
Pretexting is also a throw in of social engineering for culprits to cheat your trust.
As soon as you comply, they will use your data to execute other criminal activities.
Attackers take advantage of the curiosity and greed of human nature to put in their login credentials.
Therefore, dont download any free music or movie via strange websites.
Quid Pro Quo
Quid Pro Quo is a kind of social engineering which is similar to baiting.
They may claim that they are the staffs of some authoritative organizations such as Social Security Administration.
Fraudsters steal your identity information by setting up a fake website that looks like a reliable one.
Phishing
Is phishing a social engineering attack?
Of course, it is!
Phishing is the most common punch in of social engineering.
It Might Be the Phishing Scamtakes YouTube email as an example to show the danger of suspicious emails.
How Can You Protect Yourself from Social Engineering Attack?
After knowing what social engineering attack is, you must be curious about how to protect yourself from it.
Enterprises and users are supposed to pay attention to being attacked by social engineering.
Usually, the tricks include spelling mistakes or changed domain names thus they are frauds.
To avoid getting hooked, you had better try the next methods.
It adds an extra verification layer when you access certain programs.
To access these programs, you must verify some questions besides typing your user name and password.
Microsoft’s Multi-Factor Authentication service strikes again, causing many problems for a number of Office 365 users.
Method 2: Think Before You Click
There is no such a thing as a free lunch.
Refuse to click untrusted links because legal firms and associations dont need to contact you for help.
Pay attention to those suggestions like helping to restore your credits scores.
Most malicious emails can be stopped by this feature.
The criminals are so tricky that they will try the same credentials on your other accounts.
What to Do If Encountering Social Engineering?
Fix 1: Change Your Account Password
Changing all your account passwords is the most recommended.
The countermeasure and judicial action depend on the extent of the damage that the social engineering accidents have caused.
They tend to attack the people in the same organization.
In the final analysis, it is the data security that matters most in todays information age.
Therefore, here comes the question how to keep your data safe and be a lucky victim?
How to Keep Your Data Safe?
It is freeware that can be used to back up data in files & folders and partitions & disks.
Download and install this free file backup software and run it.
Click onKeep Trialto begin the journey of backup.
ClickBackupto pop launch the backup feature.
HitSourceon the left and chooseFolders and Filesin the popping-up window.
View the source and choose the desired files or folders you want to back up and tap onOK.
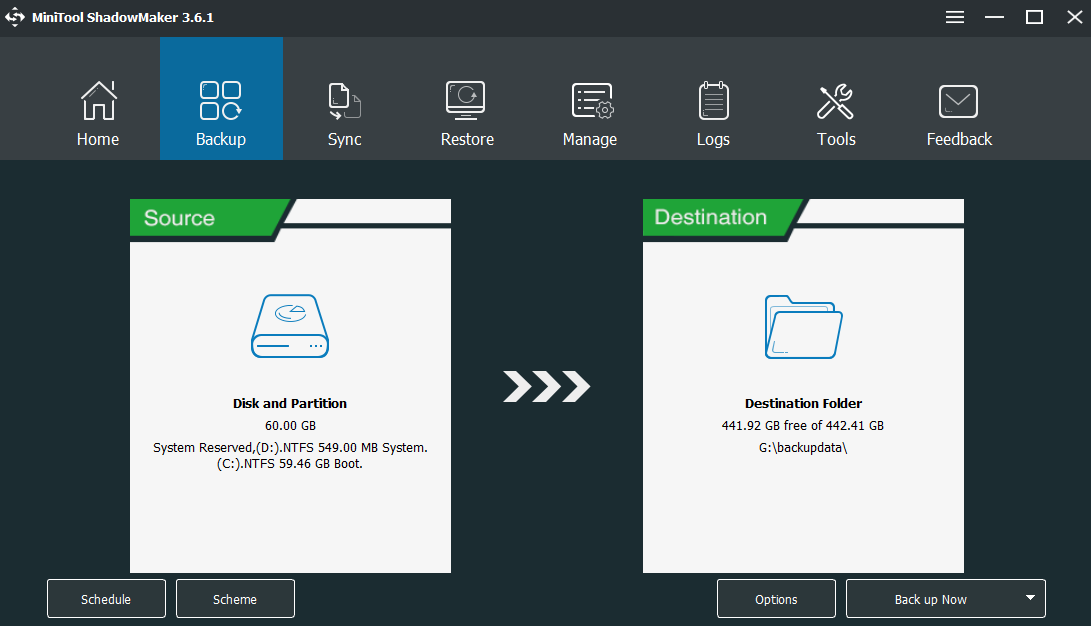
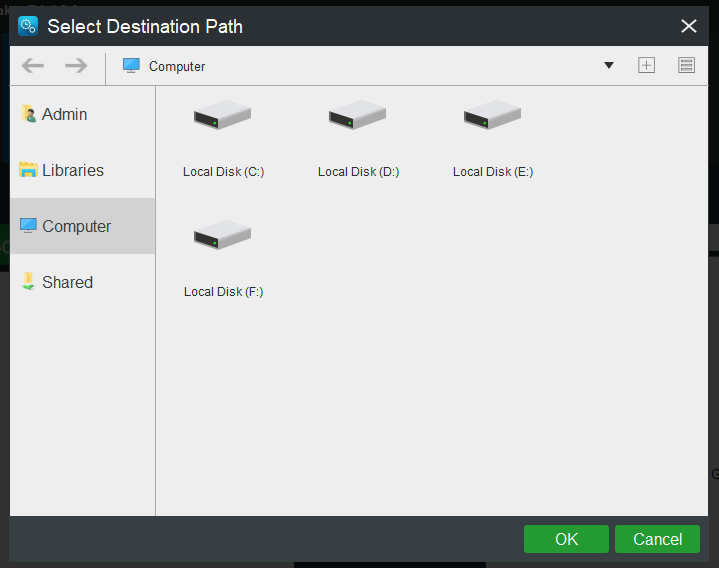
Return to the main interface ofBackup, clickDestinationto choose a destination path.
After selecting the desired location, clickOK.
ClickBack up NoworBack up Later.
The backup result will be shown inManage.
for resist the attack of social engineering, you should make full preparations for urgent situations.
MiniTool Power Data Recovery TrialClick to Download100%Clean & Safe
Step 1.
Download and install MiniTool Power Data Recovery Trial and open it.
Choose the inaccessible or damaged drive that was destroyed by attackers to scan.
It is highly recommended to recover data from theMore Lost Filesfolder.
grab the wanted ones and save them to another drive.
What is the most effective way to detect and stop social engineering attacks?
I believe your answer is very clear now.