What Does a Hacker Do?
They hide in the dark, lock their attacking targets, and easily infiltrate victims systems.
So, the danger persists.
They normally have been equipped with well-trained brains and skills.
For specific information about different types of hackers, c’mon keep reading.
Types of Hackers
White Hat Hackers
Are all hackers bad?
We call them ethical security hackers or white hat hackers.
They will mimic all the possible hacking techniques to identify security vulnerabilities that the current system has.
By doing so, people can take prompt measures to enhance the security weakness.
Different from other hackers, white hat hackers often adhere to a well-developed moral compass and law-based regulations.
They can make use of malware, ransomware, viruses, and other tactics to disrupt a systems defense.
They may play as computer hackers or security experts to execute a series of hacking activities.
Those moves, sometimes, may violate laws or ethical standards but should not be identified as malicious.
The hackers normally operate in the nebulous area and dont have malicious intent typical of a black hat hacker.
They hold disparate intentions in a state of opposition.
Green Hat Hackers
Another bang out of hacker hat is green hat hackers.
So, in their hackings, many mistakes will happen and even cause irreversible damage by accident.
These kinds of hackers normally have professional backgrounds and are invited to join corporations or organizations.
This appellation is not widely recognized so, many people will confuse them with white hat hackers.
Those hackers can also performdistributed denial-of-service (DDoS) attacksto force their competitors out of the game.
Once, more than four million such attacks were launched targeting the global gaming community.
With the high value of the video game industry, many hackers have shifted their focus to this field.
Hackers often use this name with contempt because they use hacking tools with little understanding.
Script kiddies are often ignored but they are dangerous with bad intentions to compromise other peoples computer systems.
Hacktivists
Hacktivists are more serious than other types of hacker attacks.
They start the attack not for the lure of money but for political or social causes.
The participants will leverage digital techniques to present their discontent and resistance.
In this way, they can put a spotlight on a social or political event.
Government departments and organizations are the main targets for those hackers, not just attacking them but defacing them.
It is hard to judge their positions.
They often infiltrate ones computer by seducing victims to unwittingly install a program with malicious scripts.
They are regarded as one of the most dangerous types of threat actors.
We judge them for who they are according to what they expose.
Cyberterrorists
Cyberterrorists refer to a more extensive definition includingcyber-attacksthat intimidate or generate fear in the target population.
Different organizations have varied definitions of cyberterrorism.
For example, some organizations think the cyber activities that have threatened peoples lives can be called cyberterrorism.
Botnet Hackers
Botnets are built to grow, propagate, and automate to assist large attacks.
Thats why botnet hackers can carry out high-volume attacks, jeopardizing a large number of web link systems.
How to Protect Yourself from Hackers?
Faced with so many threats, we need to take some measures to better protect ourselves from hackers.
Use antivirus and firewall to performreal-time protection.
Perform regular updates for your system and other devices.
Use dual-factor authentication as an extra layer of security for your online data.
Dont access important data related to privacy or financial information via public Wi-Fi.
Disable some useless connections, such as GPS, wireless connection, Bluetooth, or geo-tracking.
Think twice before you install an app, especially those with an unknown source.
If you cant be certain of its authenticity, just dont install it.
Keep skeptical of any links and attachments.
Use a strong password andencrypt the private dataon your unit.
Be aware of email messages from unknown parties and some phishing emails may mimic someone you know.
You should keep your eyes open for the suspicious contents.
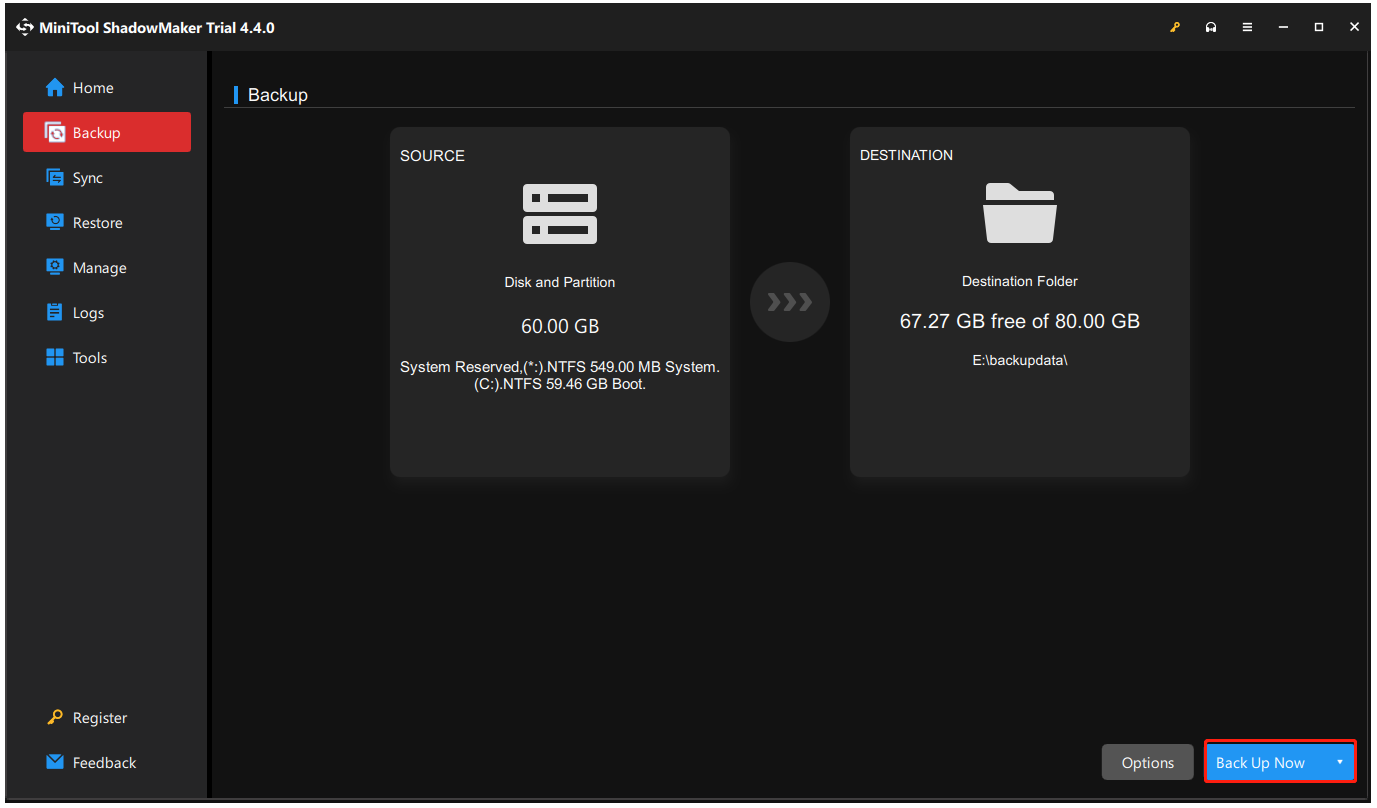
Back up your data or system; rebuild it when necessary.
Then, we recommenddata backupas your last resort to minimize your loss.
you’re able to prepare an external hard drive for data backup, which can directly avoid hacking.
In case of severe issues due to hackers, youd better try this one.
It is worth trying to keep your PC protected with a higher level of data security.
Have you ever worried about your private information being divulged?
There is a comprehensive online privacy guide for you to protect your information.
Bottom Line:
This article has introduced all the common types of hackers.
They have different purposes and apply varied techniques for the infection.