Memory regions like SMM (System Management Mode) memory contain lots of sensitive contents.
However, they may get damaged/lost due to certain reasons.
We analyzed this new variation of the Spectre attack.
There are usually lots of sensitive data kept in your computers SMM.
Like other data, they may get lost or damaged suddenly due to different reasons.
Therefore, this article analyzes the possibility and steps torecover data from SMM mode.
Youre advised to askMiniToolfor help when encountering disk problems.
The new system of speculative execution attacks is able to avoid the hardware-based memory protections.
It is reported in a previous research that one of the codes was changed by the Eclypsium team.
Whats the purpose of modifying the public proof-of-concept codes?
hey note: SMRAM refers to thephysical memoryin which the working data is saved and run by SMM.
hypervisor, operating system, or program).
It also provides access to interfaces at a higher privilege level, such as software SMI.
In this way, the top-secret SMM code and data will be revealed.
As a result, the related SMM vulnerabilities and secrets stored in this area will also be leaked.
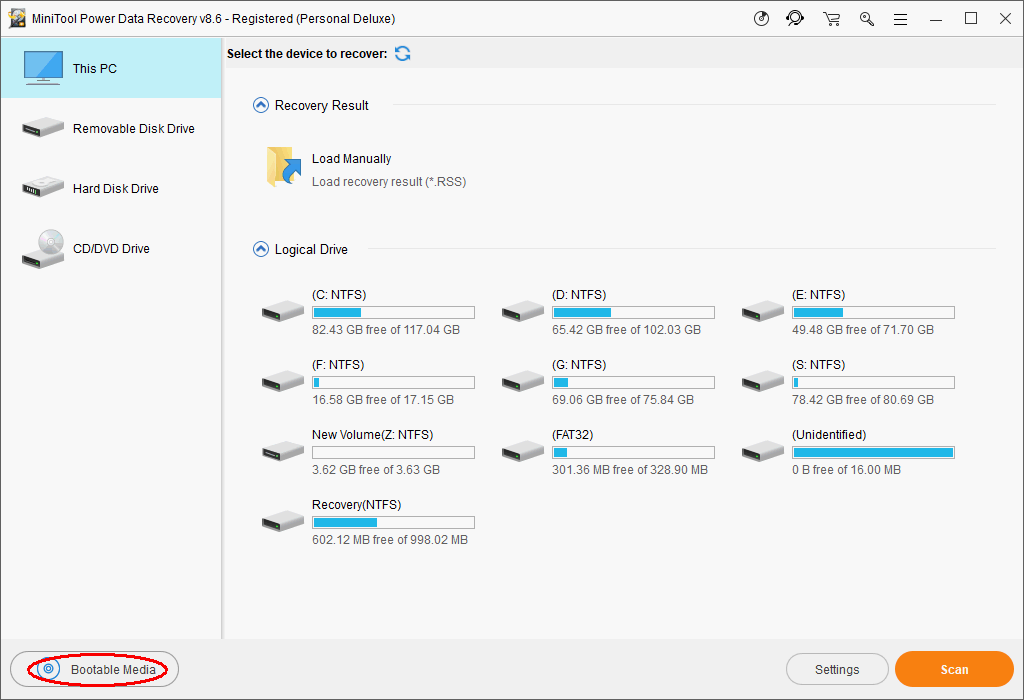
Step 1: create a bootable disk (CD/DVD/USB flash drive).
Step 2: change boot sequent in BIOS.
How to fix if your PC cant boot after BIOS update.
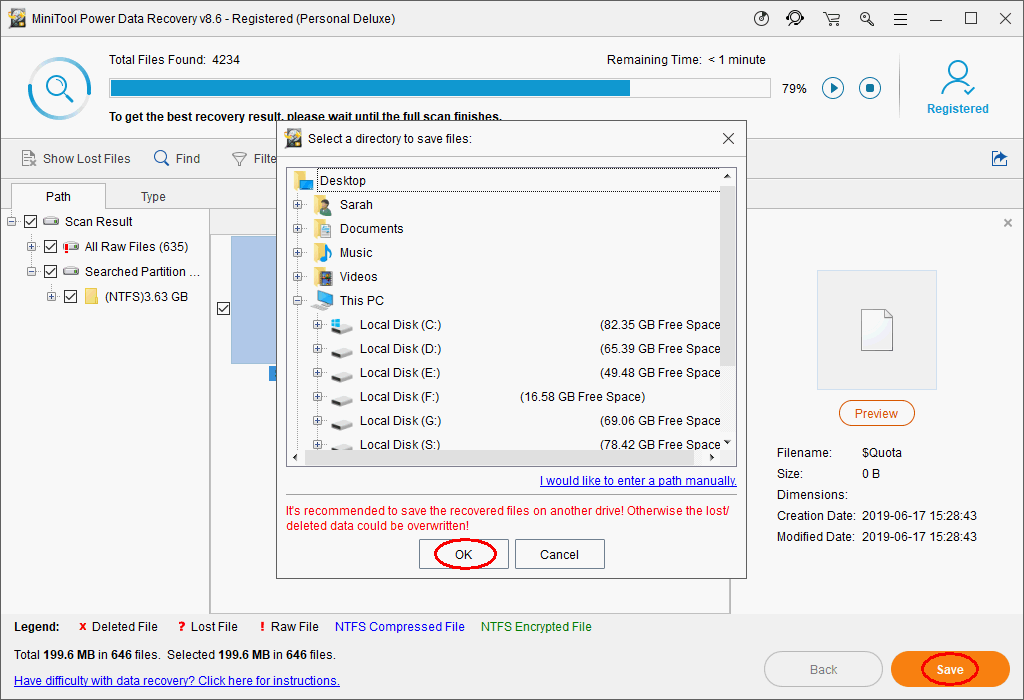
Step 3: scan the internal drive and recover files from it.
The select files have been saved to *).
You should clickOKand try useful solutions to repair the unbootable computer.
Click to Tweet
If you doubt about this program, just use the trial edition first.
In the early 90s of last century, the SMM was firstly introduced with the Intel 386SL.
To be precise, SMM is an operating mode of the x86 central processor units.
Your operating system will be suspended whenever SMM receives a code.
What happens during the interrupts?
In short, your hardware will run smoothly and all the software included will run.
Contained in the firmware or a hardware-assisted debugger, the SMM works as an alternate software system.
you might only access and execute the System Management Mode when you get high privileges.
The SMM is so important that anyone is not allowed to access it for both maintenance and security reasons.
So where is the SMRAM?
In fact, it is contained in the computers RAM.
Whats the function of SMRAM?
It is capable of executing SMI handler.
Should SMRAM be accessed all the time?
The SMRAM should be accessed when the system is contained in SMM.
In summary, the key point is whether the D_OPEN bit is set in the chipset or not.
What about the protection mechanism?
In fact, the D_LCK bit is used as the main mechanism to prevent modifying SMI handler.
If you ask me where the configuration bits are, they are located in the chipset.
And Intels response to this issue is get the original patches of Spectre variant 1 and variant 2.
They said this would be enough to stop the attack chain.
We value our partnership with the research community and are appreciative of Eclypsiums work in this area.
said a spokesperson of Intel
In fact, a report from Eclypsium discuss deeper on the attack.
As a result, the Spectre variant 1 should be migrated by using LFENCE instructions.
When it comes to the firmware from different system manufacturers or independent BIOS vendors, it is also suitable.
In addition, the mitigations have also been introduced to other Spectre attacks by the vendors.
For most firmware, it will map the physical memory to SMMs page table.
Hence, the influence will be decreased greatly.
Therefore, it is suggested that firmware developers should keep this feature in the later versions.
This is significant for protecting users from current and other SMM vulnerabilities.
This post tells you how to recover data from SMM mode and how to protect the SMM memory effectively.