What Is Fileless Malware?
Fileless Malware Detection
What makes fileless infections so insidious is also what makes them so effective.
There are also sayings that fileless malware is undetectable.

They do have differentiation.
The biggest difference between fileless malware and in-memory malware is the method of inception and prolongation.
Most malwares infection vector will write something to the disks for itself to be executed.
Windows reboot vs reset vs restart.
Check the differences between Windows reboot/restart and reset, and how to reboot/restart computer or reset Windows 10 PC.
How Does Fileless Malware Work?

Its roots can be traced back to the memory-resident (terminate-and-stay-resident) virtual programs.
There are some fileless malware examples like The Dard Avenger, Number of the Beast, and Frodo.
Instead of working in common hard drive files, fileless malware operates in computer memory.

By hacking PowerShell, it can access just about anything in Windows.
Below is an example process for fileless attack:
Step 1.
User clicks on a link in spam email.
Website loads flash and triggers exploit.
Shellcode runs PowerShell withCMDline to download and execute the payload in memory only.
Download an in-memory execution and reflectively load code.
The payload can perform exfiltration, damage, etc.
Create an auto-start registry to invoke PowerShell with a CMD line.
Fileless Malware Spreading Process
Fileless attacks are typically used for lateral movement.
They spread from one computer to another to obtain access to valuable data across the enterprise data pipe.
Most automated malware scans cant detect command line changes.
Although a trained analyst can identify those scripts, he usually does not know where to check for them.
Get access by remotely exploiting a vulnerability and using web scripting for remote access.
Steal credentials in the same method.
Maintain persistence by modifying the registry to create a backdoor.
Steal data using the file system and built-in compression utilities.
Then, upload data from the infected computer viaFTP.
If your PC is infected with Powershell.exe virus, your PC may act strangely.
Luckily, you’re free to find fixes to remove the virus in this post.
Fileless Malware Protection
How to Avoid Being Infected by Fileless Malware?
Then, how to achieve that?
Also, youd better not open attachments from unknown senders.
Thus, you might investigate every phase of the campaign before, during, and after an attack.
How to Remove Fileless Malware?
Fileless malware is a kind of malware that makes use of legitimate applications to infect computers.
It relies on no files and leaves no footprint.
Thus, it is difficult to detect and remove the fileless malware.
Actually, just reset Windows to factory default parameters orreinstall the systemcan help you rebuild your memory.
The computer is running slower, and the possible reason is the lack of RAM.
This article briefly introduces how to clean RAM.
How to Save Data from Lost During Fileless Malware Attack?
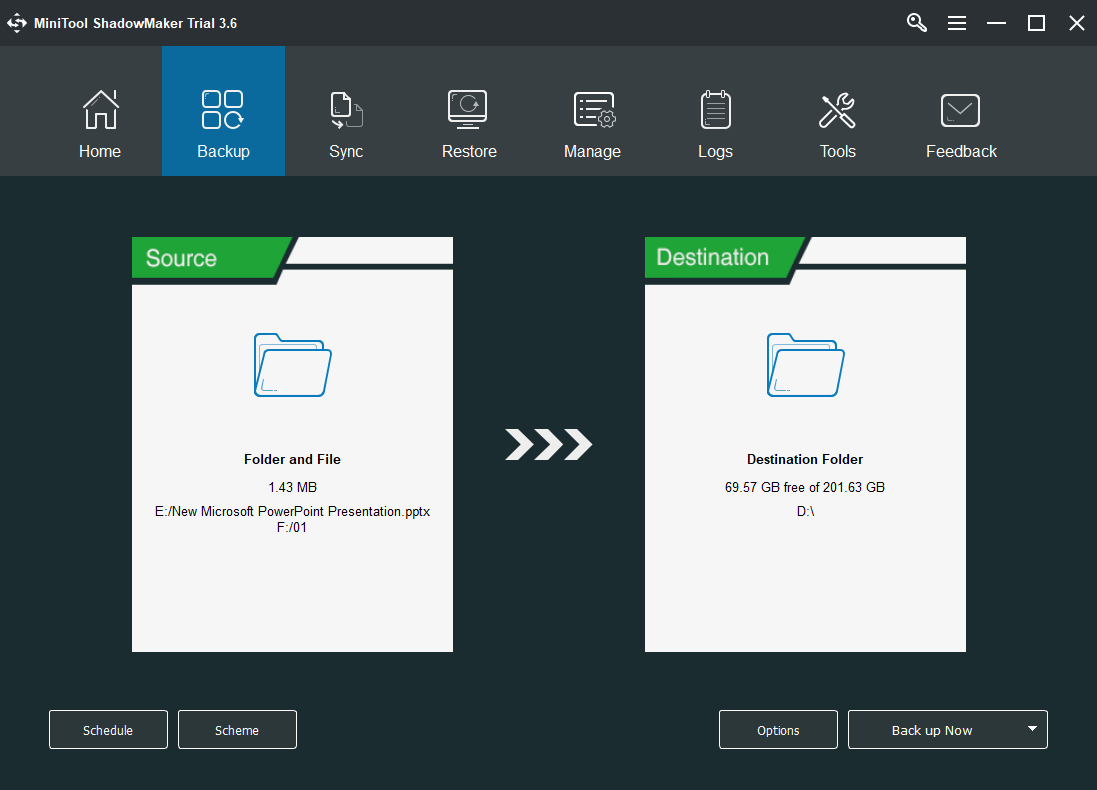
Download and install MiniTool ShadowMaker on your machine.
Open it and clickKeep Trialif you are asked to buy.
ClickBackupin the top menu of the main interface.
Click theSourcemodule in the Backup tab and select which files or programs you want to back up.
you could also choose toback up the system, a partition/volume, or a whole hard drive.
Click theDestinationmodule to select where youd like to store the backup image file.
External storage space is recommended.
Preview the backup process and confirm it by clicking theBackup up Nowbutton.
It will pop up asking for your confirmation again, just approve it.