You will have a comprehensive understanding of it after reading the article.
What Is ISCSI
TheISCSIis short forInternet Small Computer System Interface.
The ISCSI is often used to boost data transfer over intranets and to manage storage via long distances.
-image from unixmen.com
It can encrypt the online grid packets and decrypt when it arrives the destination.
Besides, it also can help you enable location-independent data storage and retrieval.
The ISICSI protocol plays a vital role in many different web link configurations.
The following content will talk them separately so that you might understand them better.
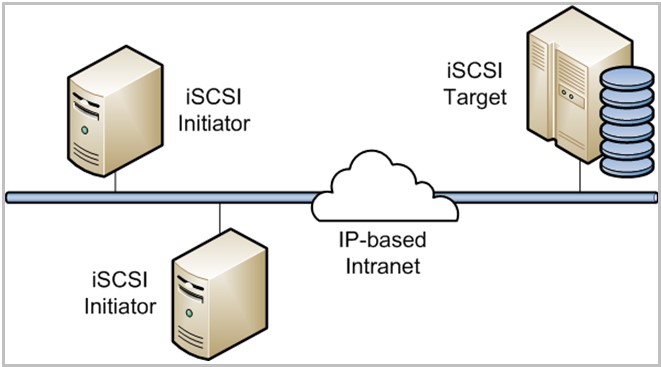
ISCSI Initiator
The client in the ISCSI storage connection is called ISCSI initiator (node).
The ISCSI initiator can connect to server (ISCSI target).
By doing so, the ISCSI initiator will sendSCSIcommands to the ISCSI target.
Due to this reason, these commands usually are contained in IP packets.
Both the ISCSI hardware initiator and ISCSI software initiator are available for you.
Thanks to some extra configuration effort, booting from the web link with the ISCSI software initiator becomes possible.
Compare with ISCSI hardware initiator, the ISCSI software initiator is less expensive.
And the ISCSI software initiator is widely distributed and stable.
ISCSI Target
The server in ISCSI storage online grid is often called ISCSI target (node).
The ISCSI target can offer you one or more so-called logical units (LUs).
The LUN you see is often used for the term logical unit, which indicates the LU number actually.
You should pick ISCSI in the situations below.
How much do you know about its performance?
If you are not clear, just read this with attention.
Of course, other elements can also affect the performance of the ISCSI.
For instance, the multipathing and Jumbo frames can also have impact on the ISCSIs performance.
The Limits of ISCSI
As you know, the ISCSI can offer you much convenience.
However, it also has some limits in itself.
Besides, as ISCSI is prone to packet sniffing, the security is annoying.
Packet sniffing is the cyberattack that you may encounter when moving across a vulnerable online grid.
Given to that fact, it’s crucial that you take some measures when utilizing ISCSI.
For example, skip additional security measures or simply the ISCSI management.
Fortunately, its advantages surpass the disadvantages.
Whats more, you’ve got the option to take some actions to avoid the drawbacks.
So, you’re able to enjoy the ISCSI service without much concern.