Malware is designed to damage your box systems and there are different types of malware.
This post fromMiniToolprovides detailed information about the types of malware.
Besides, there are some useful tips for you to avoid malware.

Now, keep on your reading.
What Is Malware
What is Malware?
Malware is software designed to damage computers and computer systems.
It is used to bypass access control to damage computer functions, and steal data.
Malware can cause damage and destruction to your organization.
Some people may ask what are the 4 types of malware or what are 5 types of malware.

Actually, there are many types of malware and they are increasing every day.
Now, lets see some common types of malware.
The 9 Common Types of Malware
Types of Malware
1.
They can quickly infect a large number of computers, consume bandwidth, and overload the webserver.
They can also encrypt data for ransomware attacks, steal information, delete files, and create botnets.
Adware
Have you ever noticed an ad suddenly appeared on your system?
This may be adware.
How to remove adware from Windows 10?
After reading this post, you know some things you should do.
Just follow the guide for adware removal.
When hackers use spyware, they can access any bang out of sensitive information of yours.
Spyware can be spread by exploiting software vulnerabilities, bundling with legitimate software or Trojan horses.
It is commonly used for identity theft and credit card fraud.
Although spyware is dangerous, fortunately, it is easy to remove.
Malvertising
6.
It encrypts files on the hard drive or locks the system and displays messages.
It aims to force you to pay the attacker to release restrictions and regain access to the computer.
After paying the attacker, your system and data will be restored to their original state.
There are two general types of ransomware to notice.
The first is the locker ransomware, which restricts access to the computer or infected rig.
The second is the crypto ransomware, which restricts access to files and stored data.
This post shares several no-cost protections to help you take a proactive approach to response how to prevent ransomware.
Hybrids
Malware is also a combination of two different types of attacks.
This usually means combining worms or Trojan horses with malware or adware.
once you nail installed a Trojan horse, cybercriminals will access to your system.
Its hard to defend against Trojan horses.
Also see:WARNING: 250 Million Account Trojan Can Disable Windows Defender
9.
Bots
A zombie program is a computer infected with malware, so hackers can control it remotely.
The zombie program can then be used to launch more attacks or become part of the zombie program collection.
Botnets can spread millions of devices because they will not be discovered.
Also see:7 Best Recommended Webcam Recording Software in 2020
Now, you have known the different types of malware.
Then, you may wonder how to find and remove the malware.
If you notice the following signs, your system may be infected by the malware.
It is also a powerful tool to protect your Windows.
MiniTool ShadowMaker also supports restore Windows backup to a different PC with dissimilar hardware.
This post How Can You Do Windows Backup Restore to Different Computercan help you do that.
Now you’re free to download and try MiniTool ShadowMaker Trial Edition to do the backup task.
you could use another feature of MiniTool ShadowMaker to back up files: Sync.
Here is how to sync files:
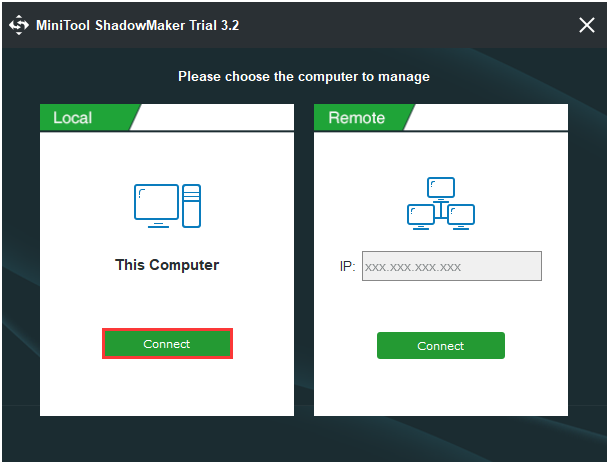
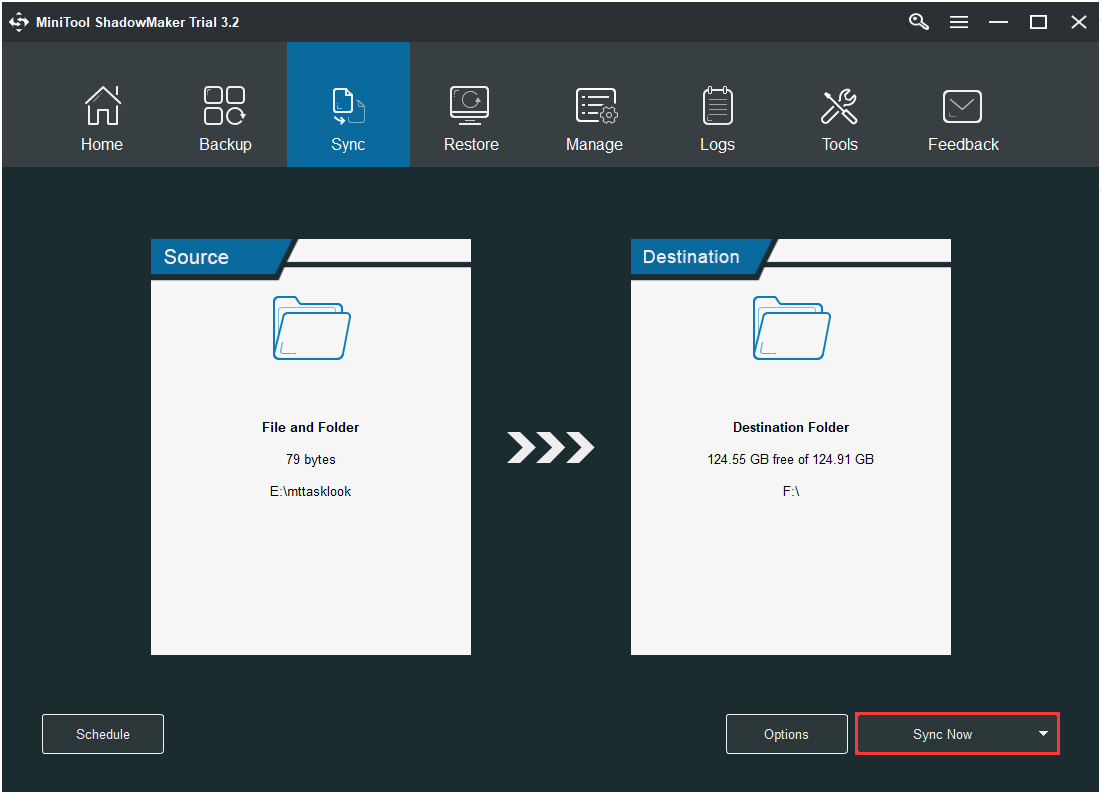
Step 1:After launching MiniTool ShadowMaker, go to theSyncpage.
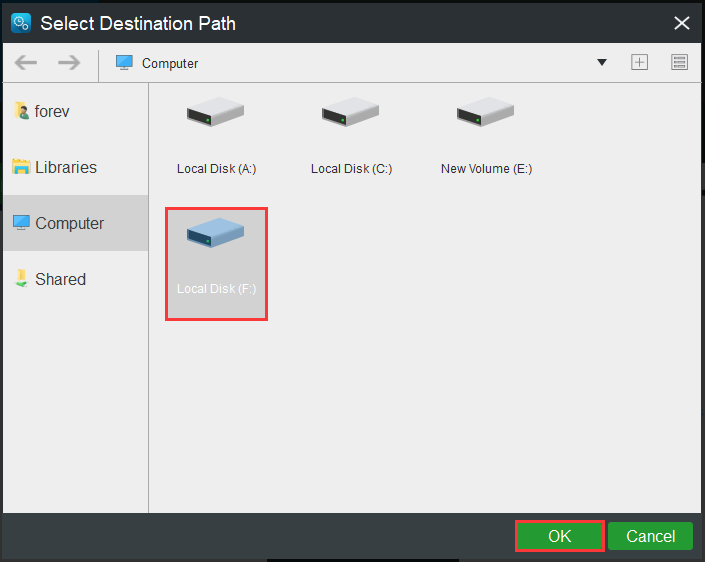
Step 2:Click theSourceandDestinationmodule to choose the files that you want to sync and the storage path.
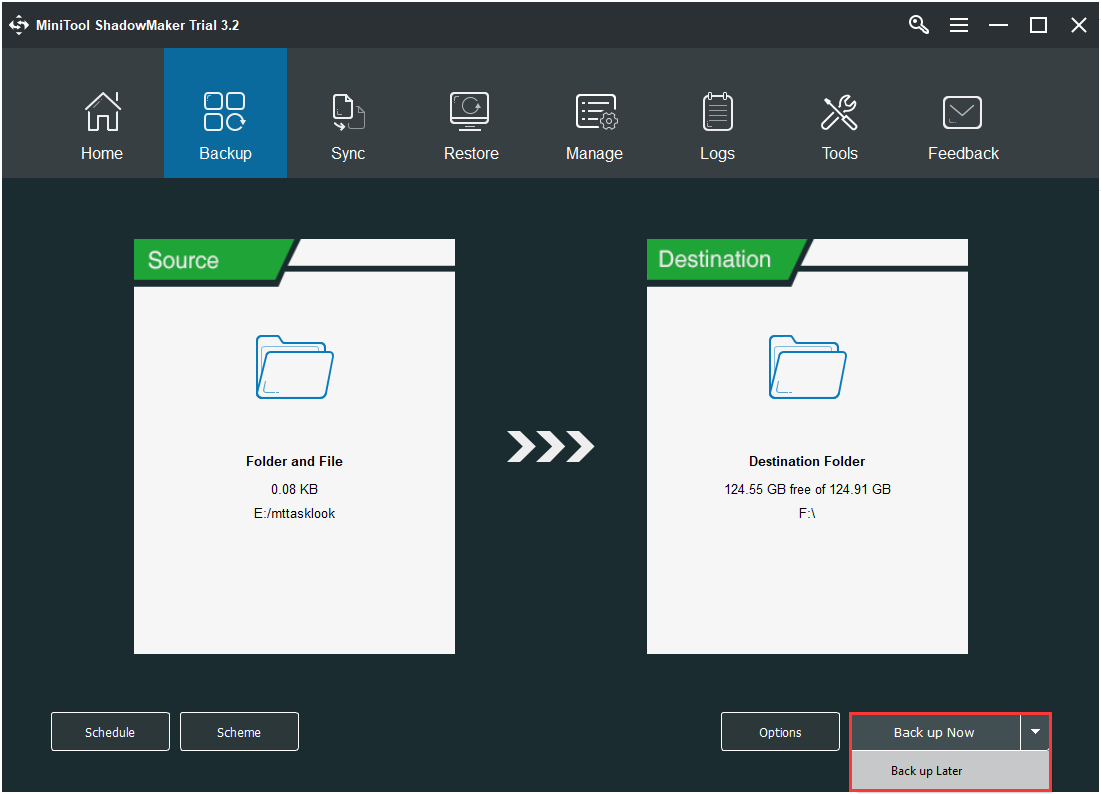
Step 3:Click theSync Nowbutton to immediately perform the sync process.
If you have any problems when you are using our program, kindly let us know.
Or if you have any suggestions, also tell us.
Sending an email to[email protected]or leaving a comment below is available.