This article composed onMiniTool official websitegives a full review on remote access trojan.
It covers its meaning, functions, bad effects, detection, removal, as well as protection methods.
Read the below content and have a deep understanding of the RAT trojan.
Remote Access Trojan Definition
What Is a RAT Virus?
RAT trojanis typically installed on a computer without its owners knowledge and often as a trojan horse or payload.
What Does a RAT Virus Do?

Many people want to set and use remote desktop in Windows 10, but dont know how.
Im writing this to help them out.
Remote Access Trojan Examples
Sincespam RATcomes into being, there have existing lots of types of it.

Back Orifice
Back Orifice (BO)rootkitis one of the best-known examples of a RAT.
Back Orifice is a computer program developed for remote system administration.
It allows a person to control a PC from a remote location.
The program debuted at DEF CON 6 on August 1st, 1998.
It was created by Sir Dystic, a member of cDc.
Though Back Orifice has legitimate purposes, its features make it a good choice for malicious usage.
It was used in targeted intrusions throughout 2015.
Sakula enables an adversary to run interactive commands and download and execute additional components.
Sub7
Sub7, also known as SubSeven or Sub7Server, is aRAT botnet.
Its name was derived by spelling NetBus backward (suBteN) and swapping ten with seven.
Typically, Sub 7 allows undetected and unauthorized access.
So, it is usually regarded as a trojan horse by the security industry.

Sub7 worked on the Windows 9x andWindows NTfamily of OSes, up to and including Windows 8.1.
Sub7 has not been maintained since 2014.
Although this RAT system was developed back in 2008, it began to proliferate at the start of 2012.
In August 2018, DarkComet was ceased indefinitely and its downloads are no longer offered on its official website.
The full list of RAT tools is too long to be displayed here and it is still growing.
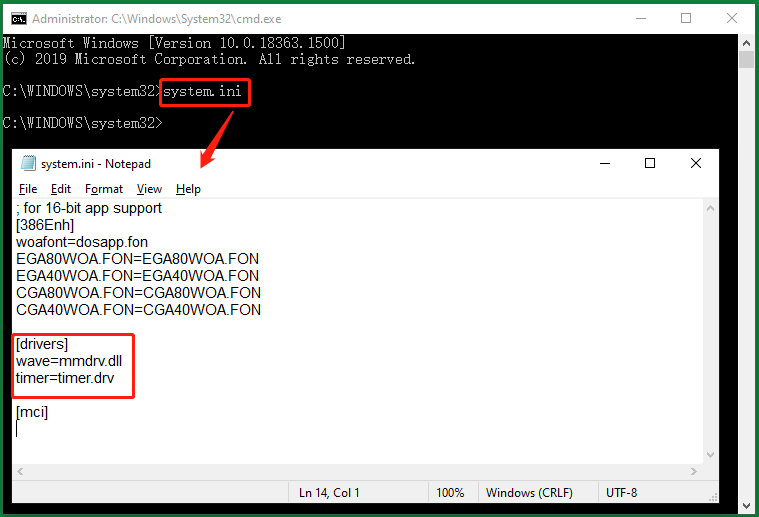
Besides,RAT spywarewill manage the use of computer resources and block the warning of low PC performance.
Then, a notepad will pop up showing you a few details of your system.
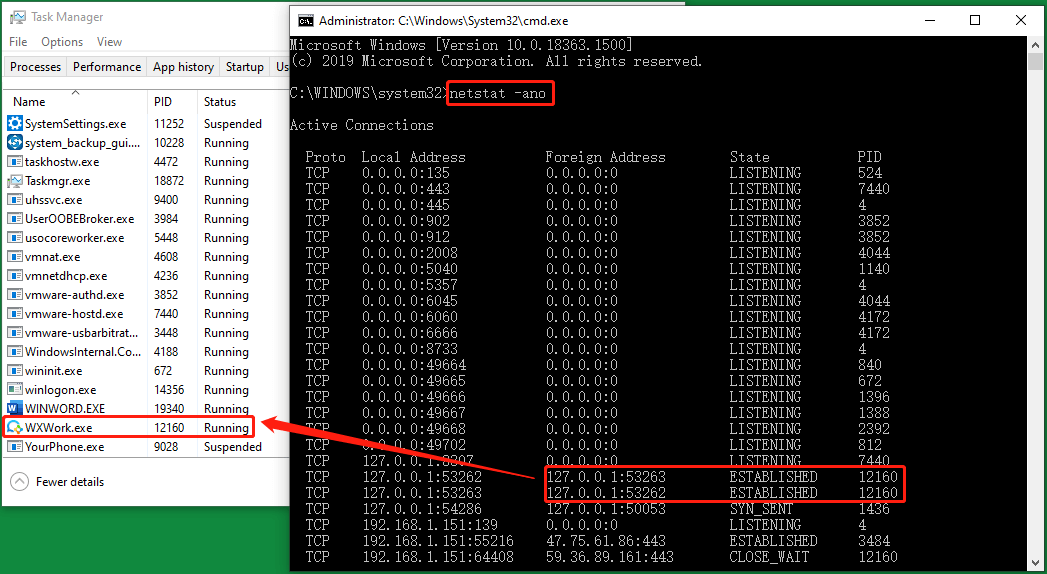
Many common security apps are goodRAT virus scannersandRAT detectors.
Then, look up the same PID in theDetailstab in Task Manager to find out the target program.
Yet, it doesnt mean the target program is a RAT for sure, just a suspicious program.
To confirm the founded program is RAT malware, further identification is needed.
Many websites that can help you do that likehttps://whatismyipaddress.com/.
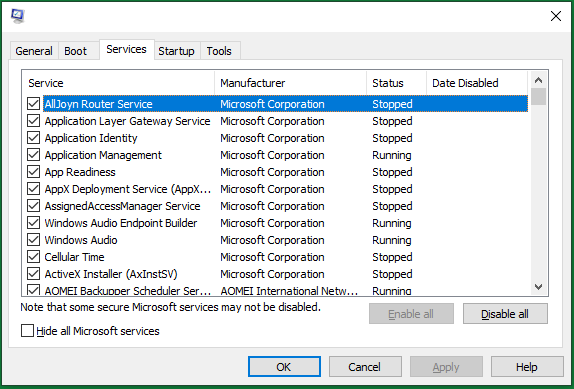
you’re able to do this in Task Manager orWindows MSConfig utility.
pop in misconfig in Windows Run and pressEnteror clickOKto trigger the MSConfig window.
There, switch to theServicestab, find the target services and disable them.
Just reset your machine after you uninstalling or blocking some programs or services.
Stage 4
Check data pipe connections going out or coming into your system that should not exist.
Or, just directly cut off your Internet connection.
How to Protect Yourself from RAT Cyber Attack?
The newest versions always adopt the latest security technologies and are specially designed for the current popular threats.
Whats spyware and malware detection?
How to carry out malware detection?
How to tell if you are infected by malware?
How to survive from malware attacks?
To upgrade the operating system to safeguard your whole machine!
MiniTool ShadowMaker TrialClick to Download100%Clean & Safe
Step 1.
Download MiniTool ShadowMaker from itsofficial websiteor the above-authorized link button.
Install and launch the tool on your PC.
If you get its Trial version, you will be prompted to buy its paid editions.
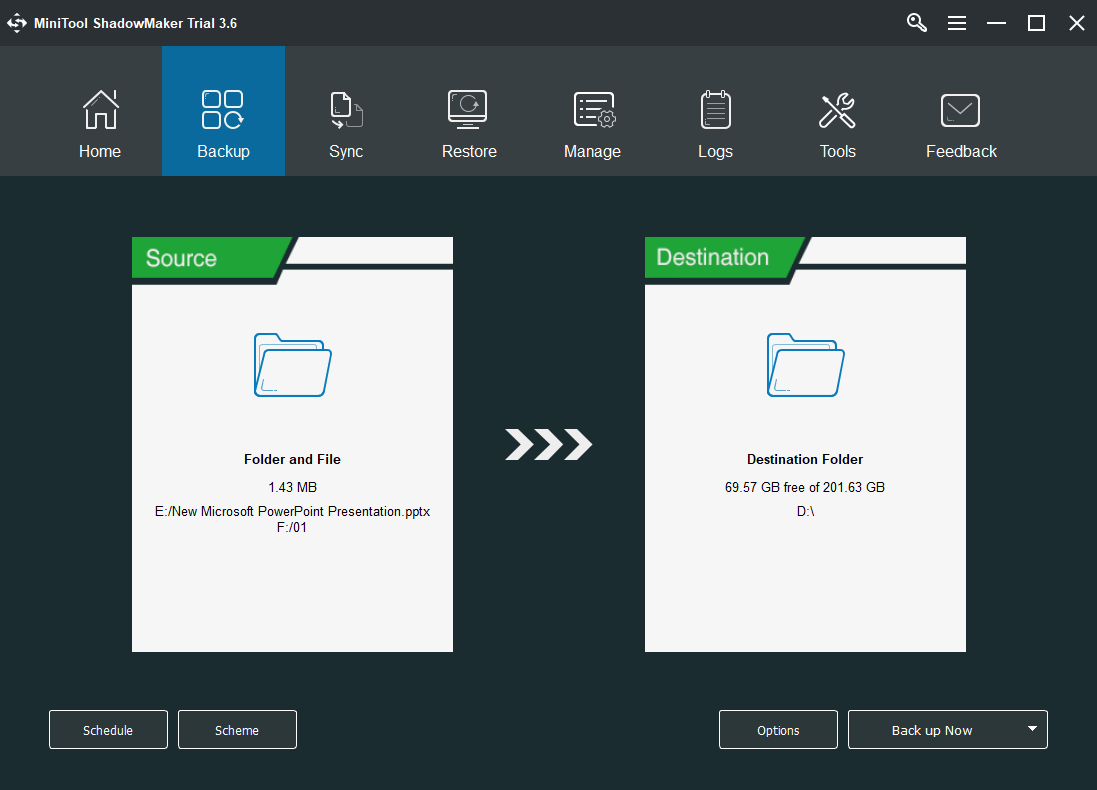
When you enter its main interface, click theBackuptab on the top menu.
Click theBack up Nowbutton in the lower right to carry out the process.
The rest is to wait for the success of the task.