What is a backdoor virus?
How does a backdoor virus do?
Most importantly, how to prevent its attack?

In this article onMiniTool Website, all the problems above are answered in detail.
If you are interested in it, follow up the guidelines in this article carefully.
What Is a Backdoor Virus?

A backdoor virus definition refers to a kind of malware that negates normal authentication procedures to access a system.
Whats spyware and malware detection?
How to carry out malware detection?
How to tell if you are infected by malware?
How to survive from malware attacks?
The malicious activities of backdoor viruses usually contain:
What is a DDoS attack?

How to protect your data and site from DDoS attacks?
If you have these questions, this article will give you a detailed guide.
These activities are so harmful that they may impact negatively on your operating system and precious personal data.

As a result, you are supposed to remain vigilant about the presence of backdoor viruses.
In this part, I will introduce to you the 4 most common backdoor viruses.
Herere 4 Solutions for You.
Trojans
Like Rootkit, Trojan can also conceal its activities.
It gets access to computers by fiddling with the verified file.
If you allow the permission, Trojans will be installed on the operating system and a backdoor is created.
At last, hackers can do anything they want to do on your machine.
What is a Trojan virus?
What does a Trojan virus do?
How to remove the Trojan virus from your machine?
This post shows you the answers.
Cryptographic backdoors access important cryptographic keys and access your information without your knowledge.
Hackers will make use of it to install a backdoor on your gadget.
Weak Password
Simple and weak passwords can be easily cracked.
Open connection Ports
Hackers usually target open connection ports because they can receive traffic from remote locations.
A port scanner can help you to find and check all the programs running on the detected ports.
Hackers may use the legitimate backdoor to attack the OS.
How to Prevent Backdoor Virus Attack?
Updating software to its latest version helps to fix these vulnerabilities.
Want to learn how to check software version?
We will help you to identify the version of software youre using on this page.
If you dont know how to create a unique password, you might rely on password managers.
It is also necessary to change your password at a regular basis.
attempt to enable Multi-Factor Authentication as much as you’re free to.
This method will help drop off the hackers when they jump into the gadget the next time.
A top password manager helps you store and manage your passwords well.
This post lists the 6 best free password managers in 2021 for your reference.
It is of vital importance to keep your Windows Defender up to date.
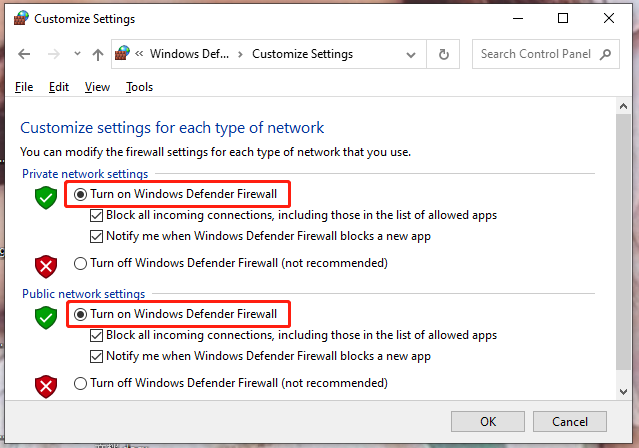
OpenControl Paneland scroll down to locateWindows Defender Firewall.
In the left pane, hitTurn Windows Defender Firewall on or off.
TickTurn on Windows Defender Firewallboth underPrivate online grid settingsandPublic online grid configs.
Dont forget to tick the box besideBlock all incoming connections, including those in the list of allowed apps.
PressOKto save the changes.
What if you want to allow certain applications through Windows Defender Firewall?
More detailed instructions are given in -How to Allow or Block a Program Through Firewall Windows 10.
Press thegear iconto openWindows parameters.
In the parameters menu, scroll down to look forUpdate & Securityand tap on it.
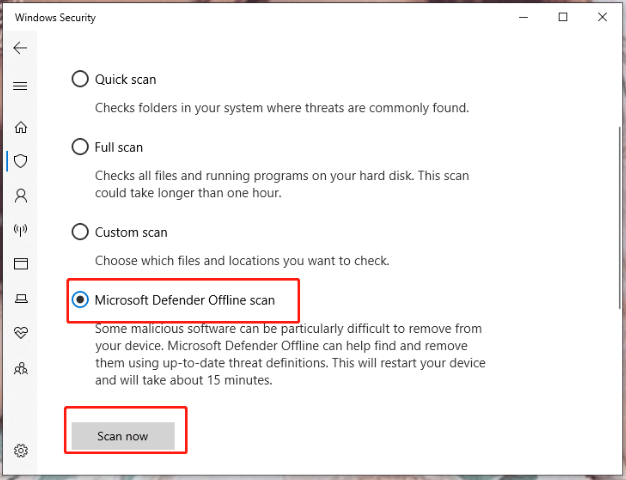
In theWindows Securitytab, click onVirus & threatprotection and chooseScan optionsunderCurrent threats.
TickMicrosoft Defender Offline scanand pressScan now.
After the scanning process is done, choose the backdoor virus files and delete them.
Do you know what the differences between antivirus software and firewall are?
If you are curious about that, go to -Antivirus vs Firewall How to Improve Your Data Security.
What is a backdoor virus?
How to prevent its attack?
I believe your answer is clear now.
Is this article useful to you?
When your system is damaged, your important data may also be destroyed or missing.
Here Are Answers and Fixes.
However, if you have backed up your setup and files, things would be easier.
you might restore these files and restore your setup to a normal state in a few clicks.
How to back up your files?
MiniTool ShadowMaker is a good option for that.
Now, let me show you how to create a file backup step by step.
Download and install MiniTool ShadowMaker.
you might enjoy its service for free within 30 days.
MiniTool ShadowMaker TrialClick to Download100%Clean & Safe
Step 2.
Launch the program and hitKeep Trial.
Go to theBackuppage and hit theSourcebutton in the left pane.
ChooseFolders and Filesand then tick the files that you want to back up.
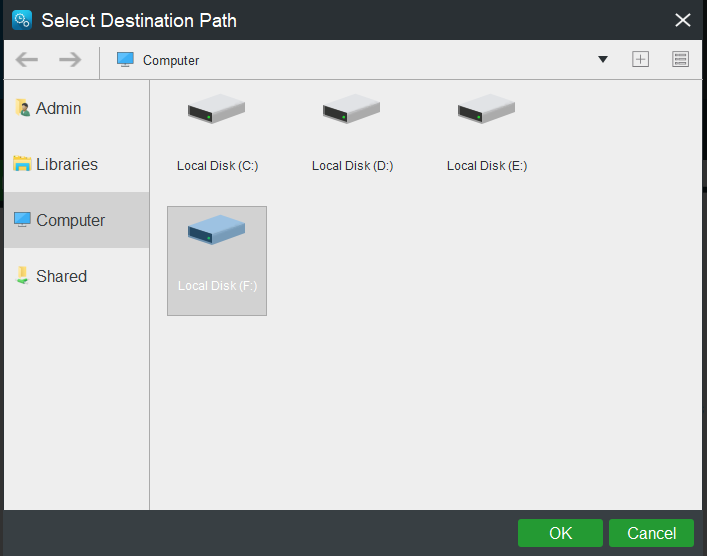
HitOKto save it and hit theDestinationbutton to select a destination path.
PressBack up Nowto start the process at once.
If you are also infected by backdoor viruses, the fixes mentioned above deserve a shot.
At the same time, more suggestions about backdoor viruses and our products are also welcomed.
you’re free to send us emails via[email protected]or make a comment below.
Meanwhile, a backdoor virus can be legitimate itself.
Developers delete it before shipping products.
Poison Tap is one of the most notorious examples of backdoors.
Once it is installed, hackers can gain root-level access to any website including those protected with 2FA.
In 2017, DoublePulsar was spotted with backdoor viruses.
It allowed others to monitor Windows PCs.
Cybercriminals can install powerful crucial cryptojacker featuring high memory to mine Bitcoin with the help of backdoor viruses.
They can get root-level access and steal your data.